Minecraft Survival Multiplayer (Java Edition)
To play on the Memory Matrix Survival Multiplayer server, use memorymatrix.cloud as the server address in the Java edition of Minecraft.
Here are the server rules:
* Any found items may be taken, including building parts and chest items.
* Do not fight players without their approval.
* No profanity or relationship chatter.
* No illegal activity.
* You play at your own risk.
* There are no guarantees or warranties.
* Unauthorized cheating, such as unauthorized flight, unauthorized creative mode, kill aura etc. will result in a ban. Elytras are fine. Shaders and resource packs are fine. No X-ray.
* Do not break or remove any railroad components such as the tracks or blocks the tracks are upon. You may use and take the mine carts themselves, but do not create any dysfunction for railways.
The server was launched in September 2025.(1) There are no longer automatic item and experience distributions unless they are specifically requested.
Complementary Unbound Shaders on Java Edition, 1.21.11, Iris & Sodium, Debian 12:
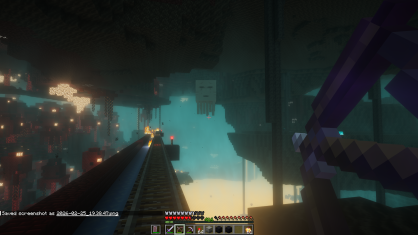
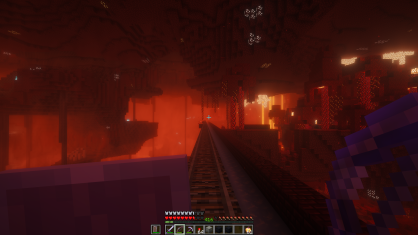
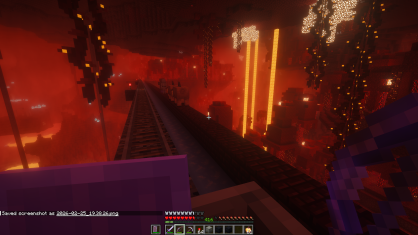
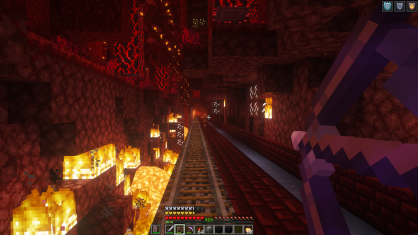
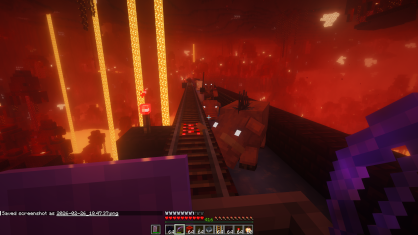
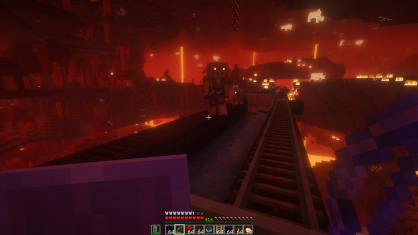
Riding the nether rail and ice road:
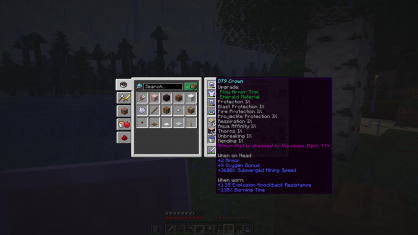
A glance at some armor that is dressed to the nines (DT9):
The server is monitored. The server uses this same address for network and cost reasons.
1. Minecraft Survival Multi-Player at memorymatrix.cloud, September, 2025, https://memorymatrix.cloud/archives/2471.html